I noticed an Inidan Gov't site in Zscaler's blocked logs from yesterday:
hxxp://www.hil.gov.in

Hindustan Insecticides Limited: A Government of India Enterprise
(I'm sure you can appreciate the irony here, as insecticides are used to kill bugs).
Viewing the source of the page, there is an embedded iframe in the beginning to:
hxxp://193.104.27.99/ad.php
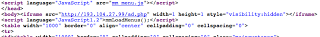
which redirects to: hxxp://cfkrdbfplrla.com/ld/tuta4/and is used to advertise A/V, registry cleaner, etc. wares through:
hxxp://www.searchmagnified.com/Free_Antivirus.cfm?domain=cfkrdbfplrla.com&foiffs=in100fweg&cifr=1&fp= ~snip~
 McAfee SiteAdvisor and other Google results for SearchMagnified lists it as being involved in some suspicious activities.
McAfee SiteAdvisor and other Google results for SearchMagnified lists it as being involved in some suspicious activities.
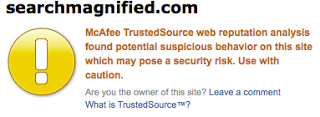
I was expecting to follow the link and reach an obvious Fake A/V page. Instead I reached:
 hxxp://www.cyberdefender.com/EDC/landing/10/?affl=tsayahooedc_antixvirusxfree&campaign_code=002048&int_page=1& ~snip~
hxxp://www.cyberdefender.com/EDC/landing/10/?affl=tsayahooedc_antixvirusxfree&campaign_code=002048&int_page=1& ~snip~
Note the affiliate ID and the campaign code in the link parameters. The SearchMagnified links are pay-per-click links, so they are making a buck off the Indian Gov't redirect when folks follow the links. The links in this case pointed me to CyberDefender, a legit A/V vendor who are paying affiliates to advertise on the web for them - the problem is that the affiliates may engage in less than legit practices (as is the case here).
Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
SuscríbaseIndian Gov't Site Victim Of Ad Campaign
Gracias por leer
¿Este post ha sido útil?

Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Al enviar el formulario, acepta nuestra política de privacidad.




