Las vulnerabilidades críticas de cortafuegos y VPN exponen su empresa a ciberataques
Es hora de una arquitectura de confianza cero.
Aproveche la oferta especial de Zscaler
¿Le preocupan los recientes CVE de cortafuegos y VPN? Zscaler ofrece una evaluación gratuita de la superficie de ataque y consultoría profesional para ayudar a las organizaciones a pasar de las arquitecturas heredadas a la confianza cero.
Los cortafuegos y las VPN crean vulnerabilidades y no proporcionan confianza cero. Aléjese de los cortafuegos y VPN heredados o en la nube y opte por Zscaler.
- Evite dispositivos expuestos o direcciones IP. Oculte a los usuarios, las sucursales y las fábricas detrás de la plataforma Zero Trust Exchange™.
- Implemente el acceso a aplicaciones de confianza cero. Conecte a los usuarios directamente a las aplicaciones, no a las redes, y elimine el movimiento lateral de amenazas.
- Obtenga una gestión integral de la superficie de ataque. Obtenga una visión global de lo que está expuesto a Internet, las vulnerabilidades y las debilidades de TLS/SSL.
Construida sobre el principio de privilegios mínimos, la arquitectura proxy de Zscaler permite inspección TLS/SSL a escala, con conexiones intermediadas entre usuarios y aplicaciones basadas en identidad, contextos y políticas comerciales.

Los cortafuegos y las VPN amplían su superficie de ataque y le dejan expuesto.
En un año ya marcado por revelaciones consecutivas de vulnerabilidades de día cero por parte de varios proveedores líderes de cortafuegos y VPN, lo último de Palo Alto Networks (CVE-2024-3400), con una puntuación CVSS de 10, es un claro recordatorio de que si usted es localizable, es vulnerable. Estas vulnerabilidades actúan como un punto de partida para que los atacantes lancen ataques sofisticados y se muevan lateralmente a través de redes planas.
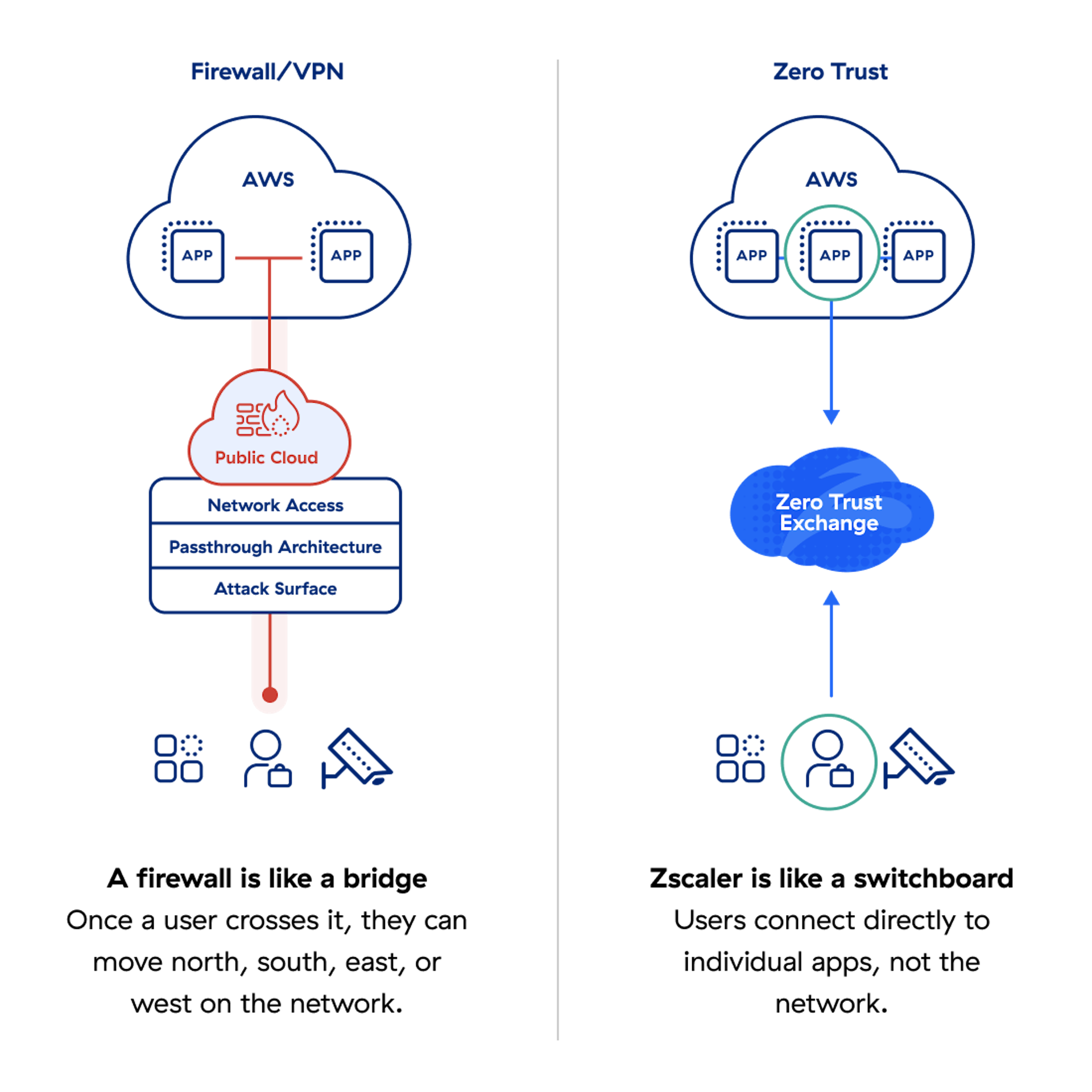
Minimiza la superficie de ataque, evita compromisos, elimina el movimiento lateral y detiene la pérdida de datos.
Elimina productos puntuales y complejidad, lo que reduce el riesgo empresarial.
Ofrece protección contra amenazas mediante IA impulsada por 500 billones de señales diarias y más de 400 mil millones de transacciones diarias
Información procesable y flujos de trabajo guiados para la corrección