/ ¿Qué es Secure Access Service Edge (SASE)?
¿Qué es Secure Access Service Edge (SASE)?
¿Qué significa SASE?
SASE (pronunciado "sasy"), o perímetro de servicio de acceso seguro, definido por primera vez por Gartner en el informe de 2019 "El futuro de la seguridad de la red está en la nube", en una convergencia de capacidades WAN con funciones de seguridad de red destinada a ofrecer a las empresas mayor agilidad, un rendimiento de red más potente y confiable, visibilidad y control más profundos y granulares en entornos de TI heterogéneos, etc.
SASE es diferente del perímetro de servicio de seguridad (SSE), que Gartner define como un subconjunto de SASE que solo se centra en los servicios de seguridad necesarios de una plataforma en la nube de SASE.
¿Cómo funciona SASE?
Una arquitectura SASE combina una red de área amplia definida por software (SD-WAN) u otra WAN con múltiples capacidades de seguridad (por ejemplo, agentes de seguridad de acceso a la nube, antimalware). La combinación de esas funciones protege el tráfico de su red.
Los enfoques heredados de inspección y verificación, como el retorno del tráfico a través de un servicio de conmutación de etiquetas multiprotocolo (MPLS) a los cortafuegos de su centro de datos, son efectivos si es allí donde se encuentran sus usuarios. Sin embargo, hoy en día, con tantos usuarios trabajando de forma remota, esta "horquilla" (retornar el tráfico de usuarios remotos a su centro de datos, inspeccionarlo y luego enviarlo de regreso) tiende a reducir la productividad y perjudicar la experiencia del usuario final.
SASE destaca entre las soluciones puntuales y otras estrategias de red de acceso seguro porque es tanto seguro como directo. En lugar de depender de la seguridad de su centro de datos, el tráfico de los dispositivos de sus usuarios se inspecciona en un punto de presencia cercano y se envía a su destino desde allí. Esto significa un acceso más eficiente a las aplicaciones y los datos, lo que la convierte en la mejor opción para proteger al personal y los datos distribuidos en la nube.
¿Es SASE simplemente una palabra que está de moda?
Si bien SASE ha atraído la atención de los proveedores de servicios y de los medios de comunicación centrados en las redes y la seguridad, lo más convincente es el principio fundamental que subyace al marco de SASE: la noción de que las arquitecturas de red y seguridad centradas en los centros de datos se han vuelto ineficaces. Esta noción no es solo un eslogan de marketing; el sector la ha aceptado ampliamente.
Así que, ¿qué ofrece una solución SASE que la hace tan valiosa en comparación con la seguridad de red empresarial tradicional que conecta oficinas a través de redes privadas y redirige el tráfico mediante puertas de enlace web seguras y cortafuegos?
Como señala Gartner, los modelos tradicionales en los que la conectividad y la seguridad se basan en el centro de datos deben centrarse en la identidad de los usuarios y los dispositivos. Según el informe, "en una empresa digital moderna centrada en la nube, los usuarios, los dispositivos y las aplicaciones a las que necesitan acceder de manera segura están en todas partes".
En otras palabras, los flujos de trabajo, los patrones de tráfico y los casos de uso actuales son muy diferentes a los que había cuando se concibieron las redes radiales. Eso se debe a que:
- Se dirige más tráfico de usuarios a los servicios en la nube que a los centros de datos
- Se trabaja más fuera de la red que en ella
- Se ejecutan más cargas de trabajo en servicios en la nube que en centros de datos
- Se utilizan más aplicaciones SaaS que las alojadas localmente
- Se alojan más datos confidenciales en servicios en la nube que dentro de la red empresarial
Los componentes de un modelo SASE
SASE se puede dividir en seis elementos esenciales en términos de sus capacidades y tecnologías:
1. Red de área amplia definida por software (SD-WAN)
SD-WAN es una arquitectura superpuesta que reduce la complejidad y optimiza la experiencia del usuario seleccionando la mejor ruta para el tráfico a Internet, las aplicaciones en la nube y el centro de datos. También le ayuda a implementar rápidamente nuevas aplicaciones y servicios, así como a gestionar políticas en una gran cantidad de ubicaciones.
2. Puerta de enlace web segura (Secure Web Gateway [SWG])
Las SWG evitan que el tráfico de Internet no seguro se introduzca en su red interna. Protege a sus empleados y usuarios del acceso y la infección por tráfico web malicioso, sitios web vulnerables, virus transmitidos por Internet, malware y otras ciberamenazas.
3. Agente de seguridad de acceso a la nube (CASB)
Los CASB previenen las fugas de datos, la infección por malware, el incumplimiento de las normativas y la falta de visibilidad garantizando que se usen con seguridad las aplicaciones y servicios en la nube. Protegen las aplicaciones en la nube alojadas en nubes públicas (IaaS), nubes privadas o entregadas como software como servicio (SaaS).
4. Cortafuegos como servicio (FWaaS)
El FWaaS le ayuda a reemplazar los dispositivos de cortafuegos físicos por cortafuegos en la nube que ofrecen capacidades avanzadas de cortafuegos de capa 7/nueva generación (NGFW), incluidos los controles de acceso, como el filtrado de URL, la prevención contra amenazas avanzadas, los sistemas de prevención de intrusiones (IPS) y la seguridad DNS.
5. Acceso a la red de confianza cero (ZTNA)
Las soluciones ZTNA brindan a los usuarios remotos acceso seguro a aplicaciones internas. Con un modelo de zero trust, nunca se asume la confianza y se otorga el acceso con menos privilegios en función de políticas granulares. Brinda a los usuarios remotos una conectividad segura sin colocarlos en su red ni exponer sus aplicaciones a Internet.
6. Gestión centralizada
La gestión de todo lo anterior desde una única consola le permite eliminar muchos de los desafíos del control de cambios, la administración de revisiones, la coordinación de ventanas de interrupciones de servicio y la administración de políticas, al tiempo que se aplican políticas coherentes en toda su organización, dondequiera que se conecten los usuarios.
Tres ventajas de SASE
¿Cómo puede una empresa hacer cumplir los controles de acceso y la seguridad mientras se enfrenta a estas realidades habituales? Ahí es donde entra en juego una plataforma SASE de capacidades WAN (SD-WAN) y servicios integrales de seguridad. SASE basado en la nube ofrece importantes ventajas a las organizaciones que dejan a un lado la infraestructura y la seguridad de red empresarial local y tradicional para aprovechar los servicios en la nube, la movilidad y otros aspectos de la transformación digital.
1. Reducción de los costes y la complejidad de TI
En su tarea para permitir el acceso seguro a los servicios en la nube, proteger a los usuarios y dispositivos remotos, y cerrar otras brechas en su seguridad, las organizaciones han adoptado una variedad de soluciones de seguridad, lo que añade costes y gastos generales de administración significativos. Aun así, el modelo de seguridad de red local simplemente no es efectivo en un mundo digital.
En lugar de intentar usar un concepto heredado para resolver un problema moderno, SASE da la vuelta al modelo de seguridad. En lugar de centrarse en un perímetro seguro, SASE se centra en las entidades, como los usuarios. Basados en el concepto de computación perimetral (procesamiento de la información cerca de las personas y sistemas que la necesitan), los servicios SASE acercan la seguridad y el acceso a los usuarios. Utilizando las políticas de seguridad de una organización, SASE permite o deniega dinámicamente las conexiones a aplicaciones y servicios.
2. Experiencia de usuario rápida y fluida
Cuando los usuarios estaban en la red y el departamento de TI controlaba y gestionaba las aplicaciones y la infraestructura, era fácil gestionar y predecir la experiencia del usuario. Hoy en día, incluso con entornos distribuidos de nube múltiple, muchas empresas siguen utilizando VPN para conectar a los usuarios a sus redes por motivos de seguridad. Sin embargo, las VPN ofrecen una experiencia de usuario pobre y amplían la superficie de ataque de una organización al exponer las direcciones IP.
En lugar de degradación, SASE proporciona optimización: requiere que la seguridad se aplique cerca de aquello que necesita protegerse. En lugar de enviar al usuario a la seguridad, envía la seguridad al usuario. SASE es seguro en la nube, gestiona de forma inteligente las conexiones en las centrales de Internet en tiempo real y optimiza las conexiones a las aplicaciones y servicios en la nube para garantizar una latencia baja.
3. Reducción del riesgo
Como solución nativa de la nube, SASE se ha diseñado para abordar los desafíos únicos en cuanto al riesgo en la nueva realidad de los usuarios y las aplicaciones distribuidos. Al definir la seguridad, incluida la protección contra amenazas y la prevención de la pérdida de datos (DLP), como parte fundamental del modelo de conectividad, se garantiza que todas las conexiones sean inspeccionadas y protegidas, independientemente de la ubicación, la aplicación o el cifrado.
Un componente clave del marco SASE es el acceso a la red de confianza cero (ZTNA), que proporciona a los usuarios móviles, trabajadores remotos y sucursales acceso seguro a las aplicaciones al mismo tiempo que elimina la superficie de ataque y el riesgo de movimiento lateral en la red.
¿Por qué es necesario SASE?
La transformación empresarial digital exige mayor agilidad y escalabilidad junto con una menor complejidad y una seguridad mejorada. Además, las empresas modernas necesitan asegurarse de que sus usuarios obtengan las mejores experiencias desde cualquier lugar.
Estas circunstancias han hecho que SASE pase de la categoría de "algo que es bueno tener" a "algo necesario". Estas son cuatro de las razones:
- SASE se adapta a su negocio: a medida que su empresa crece, tanto su red como su seguridad necesitan poder gestionar el aumento resultante de la demanda. SASE permite que su negocio, su red y su seguridad se ajusten a través de su modelo entregado en la nube.
- SASE hace que el trabajo desde cualquier lugar funcione: las arquitecturas radiales heredadas no pueden tolerar el ancho de banda necesario para dar a sus empleados remotos la flexibilidad que necesitan para seguir siendo productivos. SASE puede, y lo hace mientras mantiene la seguridad a nivel empresarial para todos los usuarios y dispositivos en cualquier ubicación.
- SASE hace frente a la evolución de las ciberamenazas: los equipos de seguridad están en constante alerta, defendiéndose de las últimas amenazas. SASE les ayuda ofreciendo una seguridad superior y facilidad de administración, lo que permite a estos equipos actuar frente a amenazas avanzadas, sea de donde sea que provengan.
- SASE le brinda una base para la adopción de IoT: el Internet de las cosas está fomentando la utilidad de las empresas de todo el mundo, pero para adoptar eficazmente la tecnología y las capacidades de IoT, necesita una plataforma sólida en la que construir un ecosistema de IoT. SASE le permite alcanzar sus objetivos de IoT con una conectividad y seguridad sin precedentes.
Todo esto ha impulsado a los proveedores de redes y seguridad a crear sus propias versiones de una arquitectura SASE. Muchos de estos proveedores afirman diseñar un producto en la nube, pero la verdad es que un gran número de ellos no son más que una plataforma en la nube construida sobre hardware heredado.
Solo un proveedor puede proporcionar un modelo SASE realmente entregado en la nube. ¿Por qué? Porque hemos construido nuestra plataforma en la nube, para la nube.
Zscaler SASE
Zscaler Zero Trust Exchange™ es nuestra solución SASE, que le ofrece un modelo rápido, flexible, simple y seguro para conectar usuarios y dispositivos. Nuestra plataforma es fácil de desplegar y gestionar como un servicio automatizado en la nube y, dado que está distribuida globalmente, sus usuarios están siempre a escasa distancia de sus aplicaciones.
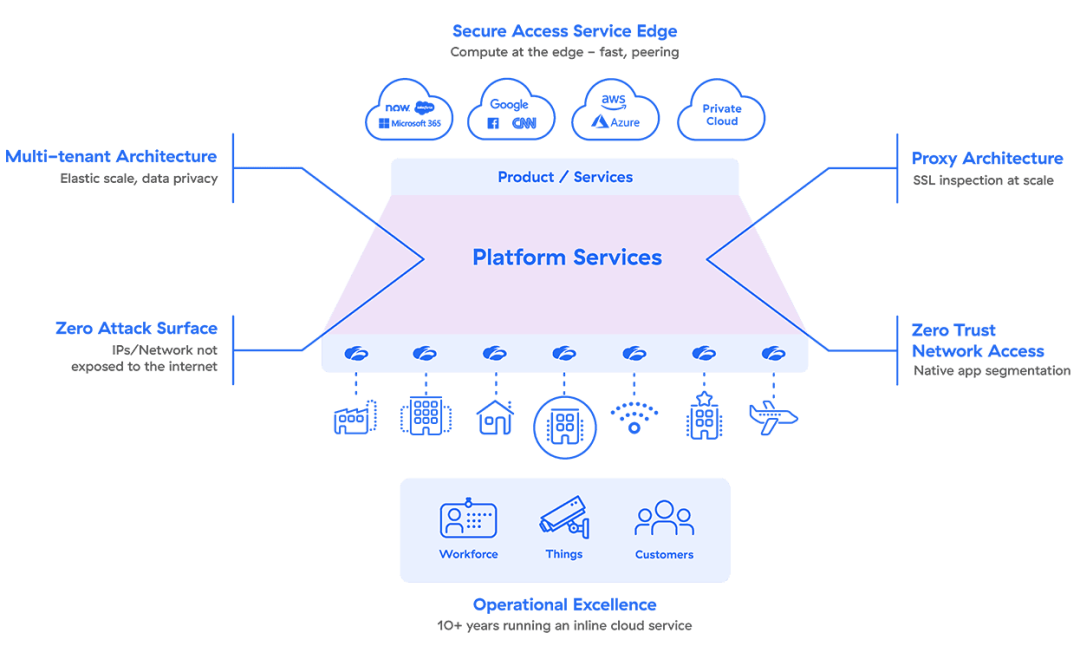
Esto es lo que hace que nuestro SASE sea único:
- Una arquitectura de nube nativa y multiinquilino que se adapta dinámicamente a la demanda
- Arquitectura basada en proxy para una inspección completa del tráfico cifrado a escala
- La seguridad y la política se acercan a los usuarios para eliminar el retorno innecesario
- Acceso a la red de confianza cero (ZTNA) que restringe el acceso para proporcionar una segmentación nativa de las aplicaciones
- Superficie de ataque cero que evita los ataques dirigidos porque sus redes e identidades de origen no están expuestas a Internet
A través de la comunicación con cientos de socios en los principales intercambios de Internet de todo el mundo, Zero Trust Exchange ofrece un rendimiento y una fiabilidad óptimos para sus usuarios.
Recursos sugeridos
Preguntas frecuentes
La tecnología de red de área amplia definida por software (SD-WAN) es una superposición de red capaz de utilizar múltiples tipos de conexiones a Internet (por ejemplo, banda ancha, MPLS, LTE) para conectar usuarios y sitios remotos a la red corporativa. Proporciona gestión y control centralizados de la red para permitir visibilidad y agilidad.
El perímetro de servicio de acceso seguro (SASE) combina la funcionalidad de SD-WAN con servicios de seguridad, como cortafuegos, puertas de enlace web seguras y agentes de seguridad de acceso a la nube, en una plataforma basada en la nube que permite una conectividad protegida y eficiente entre usuarios y aplicaciones, en cualquier dispositivo y lugar. Al integrar funciones de seguridad en la propia red en lugar de depender de las llamadas soluciones “complementarias”, SASE proporciona un enfoque más integral para la seguridad de la red.
El objetivo principal del perímetro de servicio de acceso seguro (SASE) es proporcionar conectividad rápida y segura entre usuarios y aplicaciones, en cualquier dispositivo y en ubicación. SASE está diseñado para abordar los desafíos empresariales modernos, como la creciente adopción de la nube, el aumento del trabajo remoto y el cada vez más complejo panorama de riesgos cibernéticos. Además, SASE ayuda a las organizaciones a simplificar su infraestructura de seguridad, mejorar su postura de seguridad y reducir costes con una seguridad más eficiente, escalable y gestionada de manera centralizada.



