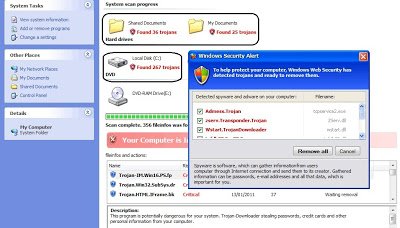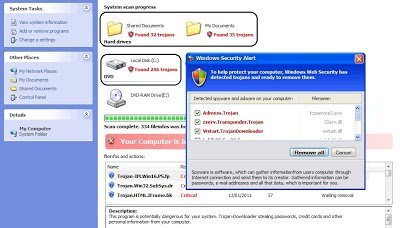
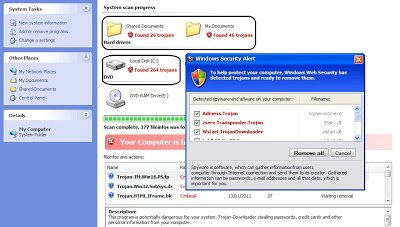
 The highlighted fake security message in the above images varies each time with different trojan count. If you look at the source code of these webpages, it has been randomized for each subsequent visit. Here is a sampling of the altered source code:
The highlighted fake security message in the above images varies each time with different trojan count. If you look at the source code of these webpages, it has been randomized for each subsequent visit. Here is a sampling of the altered source code:
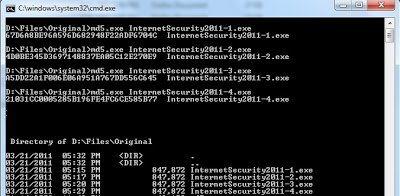
The code contains different random variables and fake security warnings, which have been split into smaller variables in an effort to evade antivirus and IDS/IPS engines that may seek to match common string patterns. As with other fake AV sites, when a victim visits the page, he is social engineered into downloading fake security software which in turns out to be malicious program. Interestingly, each time you visit this website the malicious binary changes, which results in a different MD5 hash. The size of those malicious binaries remains same. Here are the MD5 hashes for different binaries downloaded from the same website:
The Virustotal AV detection results remain very poor with only 8/43 antivirus vendors detecting the files as malicious. Here are the results for above binaries:
The example demonstrates that pure pattern matching engines will fail to detect the attack based on pattern matching strings in source code. Randomization of malicious binaries will also evade good antivirus engines.
Thanks
Umesh