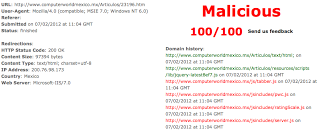
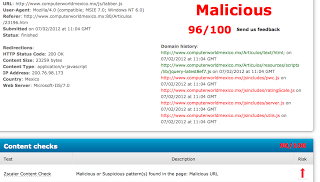
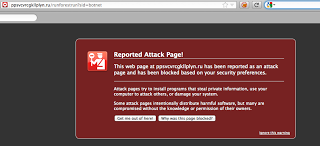
We were alerted to this from a customer reporting that Zscaler was blocking pages on www.computerworldmexico.mx
- For one, the author of the malware used Windows (you can see the carriage-return newlines as ctrl-v ctrl-M in my vi editor)
- The malicious JS utilizes the setTimeout function, so that the malicious injection only occurs after being on the page for 500 miiliseconds - which can help evade rapid, automated analysis of pages
- The malicious JS injects an IFrame using a domain generation algorithm (DGA) based on time (changes about every 40,000 milliseconds or so)