Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Suscríbase
Fake AV Copycat?
Malicious fake antivirus pages are pretty much all the same, with very straightforward code, which makes them relatively easy to detect. Most of these pages are also found just a few domains (mostly on sub-domains of xorg.pl, although the predominance of this domain has decreased lately), which makes it possible to denylist them (although this is not the best protection).
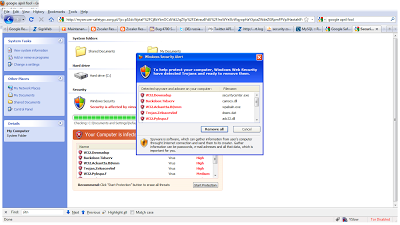
The "original" fake AV page is made of:
- a simple HTML page which displays a warning about your PC being infected, and displays a splash screen. The page title is always the same, as well as the text displayed, while the page is loading. The main page is displayed only if you come from a hacked site, direct access to the page will provide a 404 "page not found" error.
- an external Javascript file called from the main HTML page. This Javascript file contains the actual fake AV page with style sheets, images, animations, etc. It is not obfuscated.
Different display, but almost identical HTML and Javascript code
- the malicious executable is downloaded after the animation has completed, or when the user attempts to close the page
Recently however, I've seen new versions of this fake AV page start to emerge. Visually, they look the same, but they use Javascript obfuscation, and leverage new domains. Most of these new pages were not blocked by Google SafeBrowsing, even several days after we first first encountered them.
Instead of using one HTML page and an external Javascript file, all the code is on the landing page. The obfuscation uses base64 encoding in addition to custom code. It is fairly easy to decode, as it does not use eval, exceptions, DOM inspections or other tricks that break most of the obfuscation tools such as Malzilla. Once deobfuscated, the source code is very similar to what can be found in the Javascript file described above.
In addition to the code obfuscation, the page title as well as the waiting text are a little bit different from the original fake AV page. The malicious payload is detected by only 6 AV vendors out of 41. Another sample that I discovered was detected by only 2 AV vendors!
Are these new pages the work of copycats, or the next evolution from the same group of attackers? To me, it looks more like a different group of people applied simple Javascript obfuscation around the work done by others.
-- Julien
¿Este post ha sido útil?
Exención de responsabilidad: Este blog post ha sido creado por Zscaler con fines informativos exclusivamente y se ofrece "como es" sin ninguna garantía de precisión, integridad o fiabilidad. Zscaler no asume responsabilidad alguna por cualesquiera errores u omisiones ni por ninguna acción emprendida en base a la información suministrada. Cualesquiera sitios web de terceros o recursos vinculados a este blog se suministran exclusivamente por conveniencia y Zscaler no se hace responsable de su contenido o sus prácticas. Todo el contenido es susceptible a cambio sin previo aviso. Al acceder a este blog, usted acepta estas condiciones y reconoce su responsabilidad exclusiva de verificar y utilizar la información según sea precisa para sus necesidades.
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Al enviar el formulario, acepta nuestra política de privacidad.