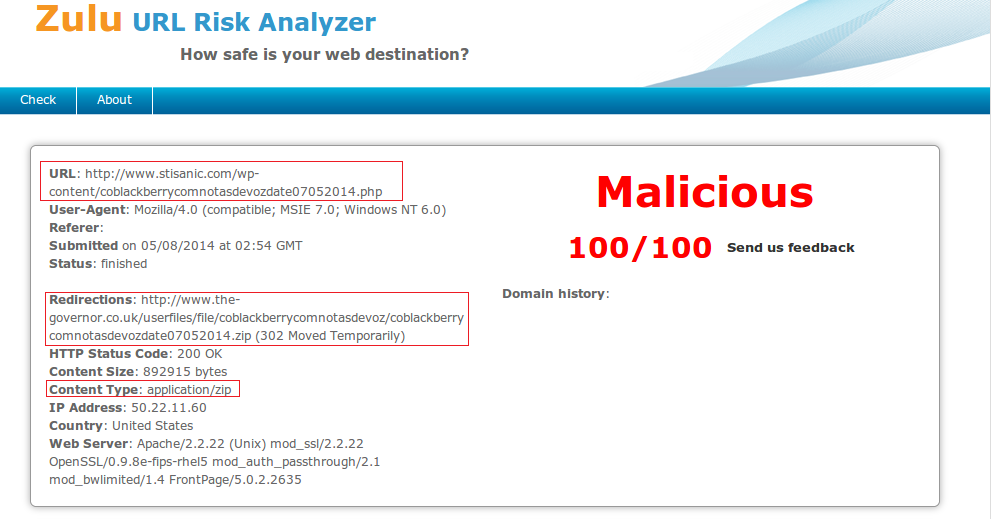
URL: hxxp://www[.]stisanic[.]com/wp-content/coblackberrycomnotasdevozdate07052014[.]php
- File : coblackberrycomnotasdevozdate07052014.zip
- md5 : d7d6574a443909b04b1ac76fb07b8dc2
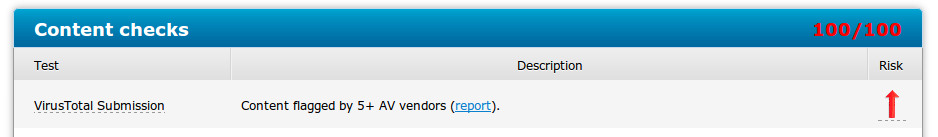
- VT Report : 10/52
- File: coblackberrycomnotasdevozdate07052014.exe
- md5: bd06e73db5b169120723206998a6074a
- VT Report: 10/52
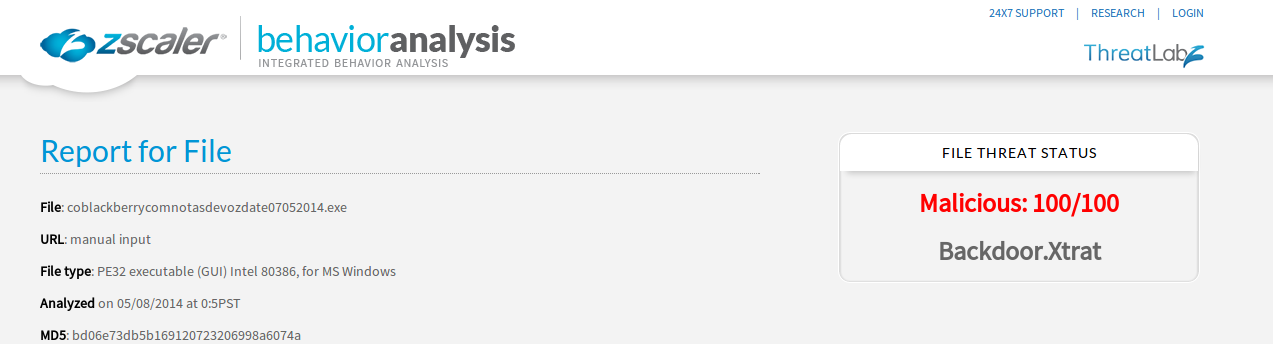 |
| Screen capture of the Zscaler Behavioral Analysis report for Backdoor.Xtrat |
Typical behavior of this backdoor:
- Injects itself into svchost.exe, exploere.exe and iexplore.exe
- Drops PE files
- Performs network activity to accept commands from a remote server and sends data to the remote server
The backdoor drops the following two EXE files on victim's machine. Both of the EXE files are same, but are dropped with different names.
- vbc.exe/wintegfire.exe
- md5 : 6fb9ce258a2420d898b6d0fa4d73bb8f
- VT Report : 6/52 (Also very less detection)
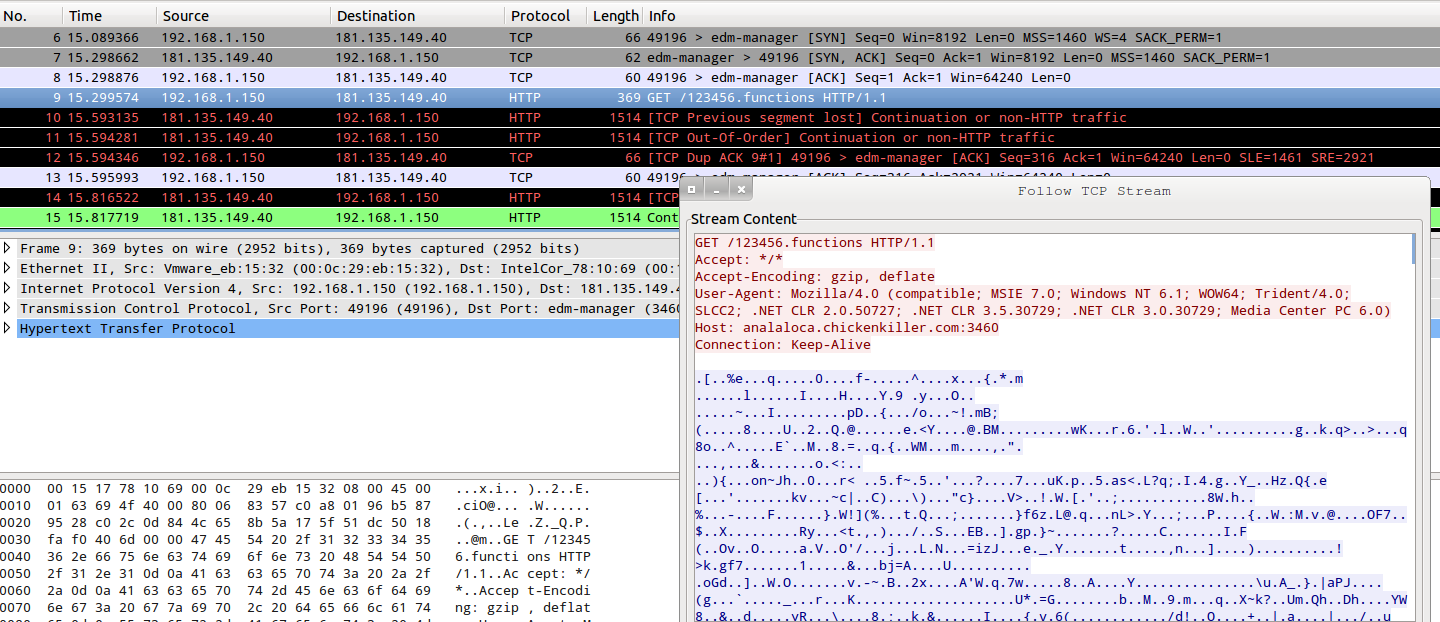
- URL: hxxp://analaloca[.]chickenkiller[.]com:3460/123456.functions
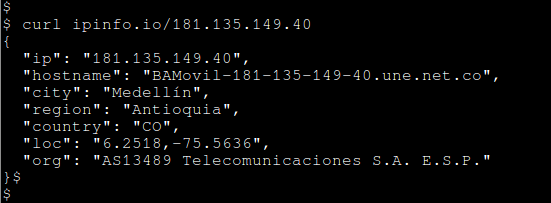
- IP: 181[.]135[.]149[.]40
- Zulu report: 100/100
CnC Server Location:
CnC URLs with the above pattern of '/123456.functions':
cascarita1.no-ip.biz:33100/123456.functions
cascarita2.no-ip.biz:33200/123456.functions
cascarita3.no-ip.biz:33500/123456.functions
windows.misconfused.org:999/123456.functions
uranio2.no-ip.biz:10180/123456.functions
fungii.no-ip.org:999/123456.functions
mohammad2010.no-ip.biz:81/123456.functions supermanaa.no-ip.biz/123456.functions
updating.serveexchange.com:999/123456.functions
spycronicjn.no-ip.org:81/123456.functions
allmyworkers.no-ip.biz:400/123456.functions
livejasminci.no-ip.biz:4444/123456.functions
31.193.9.126:3377/123456.functions
We also observed CnC URLs related to this backdoor with a small variation in the pattern. The pattern varinat observed was '/1234567890.functions'.
CnC URLs with pattern '/1234567890.functions':
suportassisten.no-ip.info:2180/1234567890.functions
laithmhrez.no-ip.info/1234567890.functions
papapa-1212.zapto.org/1234567890.functions
sarkawt122.no-ip.biz/1234567890.functions
outlook11551.no-ip.biz/1234567890.functions
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"Backdoor Xtrat URL Request"; flow:established,to_server; content:"/1234567890.functions"; http_uri; nocase; classtype:trojan-activity; reference:''; sid:YYYYY; rev:YY;)
Pradeep