Key Points
- BlackBasta emerged in February 2022 with double extortion ransomware attacks against organizations
- The threat group exfiltrates sensitive information from organizations before performing file encryption and demanding a ransom payment
- The previous version of BlackBasta shared many similarities to the now defunct Conti ransomware, although the malware code itself was novel
- In November 2022, BlackBasta ransomware received significant updates including the file encryption algorithms, introduction of stack-based string obfuscation, and per victim file extensions
- The ransomware code modifications are likely an attempt to better evade antivirus and EDR detection
Zscaler ThreatLabz has been tracking prominent ransomware families and their tactics, techniques and procedures (TTPs) including the BlackBasta ransomware family. On November 16, 2022, ThreatLabz identified new samples of the BlackBasta ransomware that had significantly lower antivirus detection rates. The latest BlackBasta code has numerous differences compared to the original BlackBasta ransomware. The changes from the previous version include replacing the file encryption algorithms and switching from the GNU Multiple Precision Arithmetic Library (GMP) to the Crypto++ encryption library. Many of the malware’s strings have been obfuscated and the filenames have been randomized, which may hinder static-based antivirus detection and behavioral-based EDR detection. This blog focuses on these recent changes to BlackBasta. Since the current BlackBasta codebase is quite different from the original, ThreatLabz refers to this new version as BlackBasta 2.0.
Technical Analysis
The following sections analyze the changes to the BlackBasta ransomware including the string obfuscation, file encryption and compare various features that have been added, removed or modified.
String Obfuscation
Similar to Conti ransomware, the BlackBasta ransomware developer appears to be experimenting with stack-based string obfuscation using ADVObfuscator. Figure 1 shows an example obfuscated string that is constructed on the stack and decoded using an XOR operation with a single byte.
Figure 1. BlackBasta 2.0 stack-based string obfuscation example
Currently, not all strings in the ransomware are obfuscated, but it is likely that more strings will be obfuscated soon.
File Encryption
Perhaps the most significant modifications in BlackBasta 2.0 is to the encryption algorithms. Previous versions of BlackBasta ransomware used a per victim asymmetric 4,096-bit RSA public key and a per file ChaCha20 symmetric key. The RSA algorithm was implemented using the GNU Multiple Precision Arithmetic Library (GMP). In the latest version of BlackBasta ransomware, the encryption algorithms have been replaced with Elliptic Curve Cryptography (ECC) and XChaCha20. The encryption library used to implement these algorithms in BlackBasta 2.0 is Crypto++. The elliptic curve used by BlackBasta 2.0 is NIST P-521 (aka secp521r1). An example hardcoded NIST P-521 public key embedded in a BlackBasta 2.0 sample is shown below:
Public-Key: (521 bit) pub: 04:00:52:1f:d8:b3:65:b7:9c:30:bd:fa:1c:88:cc: 77:77:81:f6:50:9d:d9:17:8d:17:d8:fa:3a:8c:b0: f2:6f:87:21:0c:95:db:94:f5:9c:bf:fd:ca:f0:8d: 19:6a:9c:2f:9f:4b:96:20:31:95:41:54:3e:92:43: ed:7b:d1:81:8c:58:78:01:2e:31:b8:02:7a:c1:b9: 7f:2f:b4:b2:ba:aa:df:ed:68:a2:df:eb:90:4a:4f: da:28:10:db:f5:ae:12:08:cf:dd:1f:10:80:48:00: 32:38:1d:23:40:0c:ca:05:2c:5c:d2:79:1d:ae:8f: 0a:74:a1:1c:79:b3:0c:38:21:aa:94:1a:4f ASN1 OID: secp521r1 NIST CURVE: P-521 writing EC key -----BEGIN PUBLIC KEY----- MIGbMBAGByqGSM49AgEGBSuBBAAjA4GGAAQAUh/Ys2W3nDC9+hyIzHd3gfZQndkX jRfY+jqMsPJvhyEMlduU9Zy//crwjRlqnC+fS5YgMZVBVD6SQ+170YGMWHgBLjG4 AnrBuX8vtLK6qt/taKLf65BKT9ooENv1rhIIz90fEIBIADI4HSNADMoFLFzSeR2u jwp0oRx5sww4IaqUGk8= -----END PUBLIC KEY-----
The encryption process used by BlackBasta 2.0 leverages the Crypto++ Elliptic Curve Integrated Encryption Scheme (ECIES) in Diffie-Hellman Augmented Encryption Scheme (DHAES) mode (also known as DHIES to avoid confusion with the Advanced Encryption Standard) to generate a per file XChaCha20 and a hash-based message authentication code (HMAC). BlackBasta appends a 314-byte footer to files after encryption has been completed as shown below in Figure 2.
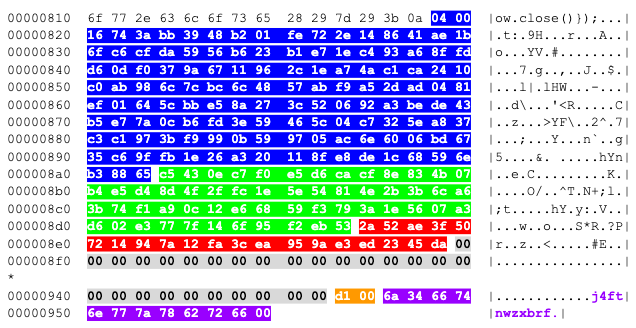
Figure 2. Example BlackBasta 2.0 encrypted file footer
The first 133-bytes (in blue) are an ephemeral NIST P-521 public key generated per file. The next 56 bytes are an encrypted per file XChaCha20 32-byte key and 24-byte nonce (in green), followed by a 20-byte HMAC (in red). This is followed by NULL byte padding and a two-byte value (in orange) for the size of the cryptographic material. The last 12 bytes (in purple) are a marker (e.g., j4ftnwzxbrf), which changes per victim that the BlackBasta decryption tool can use to identify encrypted files.
The encryption process starts by generating an ephemeral NIST P-521 key pair. The corresponding private key is then used to generate a shared secret with the hardcoded public key using the Diffie-Hellman algorithm. The result is passed to the key derivation function KDF2 to produce 72 pseudorandom bytes. The first 16-bytes are used as a HMAC key and the subsequent 56 bytes are used as an XOR key to encrypt the file’s XChaCha20 key and nonce (shown above in green). The per file XChaCha20 key and nonce are generated using the Crypto++ random number generator library. The HMAC is calculated with the ciphertext using the SHA1 hash algorithm. The result can be used for message verification with the 20 bytes in the footer (shown in red).
To optimize for speed, BlackBasta encrypts files differently with XChaCha20 based on the file's size. If the file is less than 5,000 bytes the full file is encrypted in blocks of 64 bytes. If the file size is greater than 64 bytes and not an even multiple of 64 bytes, the last 64 byte block will not be encrypted. If the file size is less than or equal to 1,073,741,824 (0x40000000) bytes (i.e., 1GB), BlackBasta alternates encrypting 64 byte blocks followed by 128 bytes that are skipped (i.e., not encrypted) until the end of the file is reached as shown in Figure 3.
Figure 3. Example file with null bytes encrypted by BlackBasta 2.0 ransomware alternating between encrypted and unencrypted blocks
If the file is larger than 1GB, BlackBasta will first encrypt the first 5,064 bytes, skip 6,336 bytes, encrypt 64 bytes, skip 6,336 bytes, and so on until the end of the file has been reached. The XChaCha20 encryption code is shown in Figure 4.
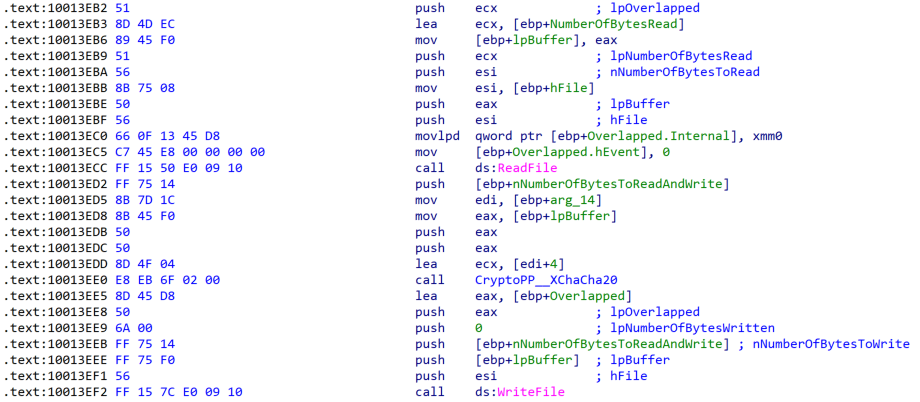
Figure 4. BlackBasta 2.0 XChaCha20 file encryption code
After encryption is complete, BlackBasta 2.0 renames the filename with a hardcoded per-victim extension such as .agnkdbd5y, .taovhsr3u or .tcw9lnz6q. The previous version of BlackBasta used only .basta for the encrypted file extension.
The encrypted ransom files’ icon image has also been modified from a white box to a red box as shown in Figure 5.
Figure 5. BlackBasta (original and new) encrypted file icon images
While this change is rather small, this may be sufficient to bypass static signatures that antivirus products may use to detect BlackBasta.
Ransom Note
BlackBasta 2.0 has modified the ransom note text as shown in Figure 6.
Figure 6. Example BlackBasta 2.0 ransom note (November 2022)
The ransom note filename has also changed from readme.txt to instructions_read_me.txt. BlackBasta 2.0 opens the ransom note in Windows Notepad via the command cmd.exe /c start /MAX notepad.exe.
BlackBasta Feature Parity
Table 1 compares the features between BlackBasta versions 1.0 and 2.0.
|
Feature |
BlackBasta 1.0 |
BlackBasta 2.0 |
|
Encryption library |
GMP |
Crypto++ |
|
Asymmetric encryption |
4,096-bit RSA |
NIST P-521 |
|
Symmetric encryption |
ChaCha20 |
XChaCha20 |
|
Change encrypted file icon |
Yes |
Yes |
|
Encrypted file extension |
.basta |
.[a-z0-9]{9} |
|
Change desktop wallpaper |
Yes |
No |
|
Readme filename |
readme.txt |
instructions_read_me.txt |
|
String obfuscation |
No |
Yes |
|
Terminate processes and services |
Yes |
No |
|
Delete shadow copies |
Yes |
Yes / No (varies between samples) |
|
Encrypted file icon name |
fkdjsadasd.ico |
fkdjsadasd.ico |
|
Mutex name |
dsajdhas.0 |
ofijweiuhuewhcsaxs.mutex |
Table 1. Feature parity between BlackBasta 1.0 and BlackBasta 2.0
In addition to the aforementioned differences, BlackBasta 2.0 no longer changes the victim’s desktop wallpaper, nor terminates processes and services that may interfere with file encryption. The mutex name has also been updated.
The number of command-line parameters has also been modified as shown in Table 2.
|
Command-line parameter |
BlackBasta 1.0 |
BlackBasta 2.0 |
Description |
|
-threads |
No |
Yes |
Number of threads to use for encryption |
|
-nomutex |
No |
Yes |
Do not create a mutex |
|
-forcepath |
Yes |
Yes |
Encrypt files in the specified path |
|
-bomb |
Yes (in newer builds) |
No |
Spread via ActiveDirectory and launch ransomware |
Table 2. Comparison between BlackBasta command-line parameters
Conclusion
Members of the Conti ransomware group appear to have splintered into multiple threat groups including BlackBasta, which has become one of the most significant ransomware threats. ThreatLabz has observed more than five victims that have been compromised by BlackBasta 2.0 since the new version’s release in mid November 2022. This demonstrates that the threat group is very successful at compromising organizations and the latest version of the ransomware will likely enable them to better evade antivirus and EDRs.
Cloud Sandbox Detection
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to BlackBasta at various levels with the following threat names:
Indicators of Compromise
|
SHA256 Hash |
Description |
|
e28188e516db1bda9015c30de59a2e91996b67c2e2b44989a6b0f562577fd757 |
BlackBasta 2.0 sample (executable) |
|
c4c8be0c939e4c24e11bad90549e3951b7969e78056d819425ca53e87af8d8ed |
BlackBasta 2.0 sample (executable) |
|
350ba7fca67721c74385faff083914ecdd66ef107a765dfb7ac08b38d5c9c0bd |
BlackBasta 2.0 sample (executable) |
|
51eb749d6cbd08baf9d43c2f83abd9d4d86eb5206f62ba43b768251a98ce9d3e |
BlackBasta 2.0 sample (DLL) |
|
07117c02a09410f47a326b52c7f17407e63ba5e6ff97277446efc75b862d2799 |
BlackBasta 2.0 sample (DLL) |
These IOCs are also provided in the ThreatLabz GitHub repository here.





