Controlling access to data collected by ZDX
In this blog post, I’d like to share details about the data that is collected and used for Zscaler Digital Experience (ZDX) and especially, the administrative means to: firstly, control what data is collected, and secondly, how to restrict access so that only defined personnel with defined roles can access and work with the data.
Information accessed by ZDX
This blog may not point out every single data point that is collected or produced by ZDX, but will give an overview of the different areas and the intention of the collection and aggregation.
The general reason for data collection is to provide performance data to inform you on the impact for the End User Experience Score (ZDX Score) and quickly identify which areas improvement actions need to be initiated.
| IT Area | Reason for data collection |
| Application | Determine if … |
| … the application itself is down or has issues. |
| … UCaaS has an issue or the network path between user and service has issues. |
| Network | |
| … there is an issue with any specific network segment and to find the owner of that network segment e.g. the ASN and the name of ISP. If those parts of the network are managed by the company itself, actions can be implemented immediately, or if contracts with the ISP exist, they can be asked to implement changes. |
| … the issues are bound to the local network. Administrators could help resolve issues that are bound to geographic areas, e.g. service down in that area. |
| Device | |
| … there is an issue with hardware usage, e.g. memory at 100%, or CPU fully loaded. |
| … there might be a software (version) that is incapable of delivering a good service. |
| … the issues are bound to the local network. Reading the location from Windows devices is an alternative to the default of estimating the location based on the IP address. |
| … there is an issue with the user’s device or its performance, and quickly identify if it is a hardware or software issue. |
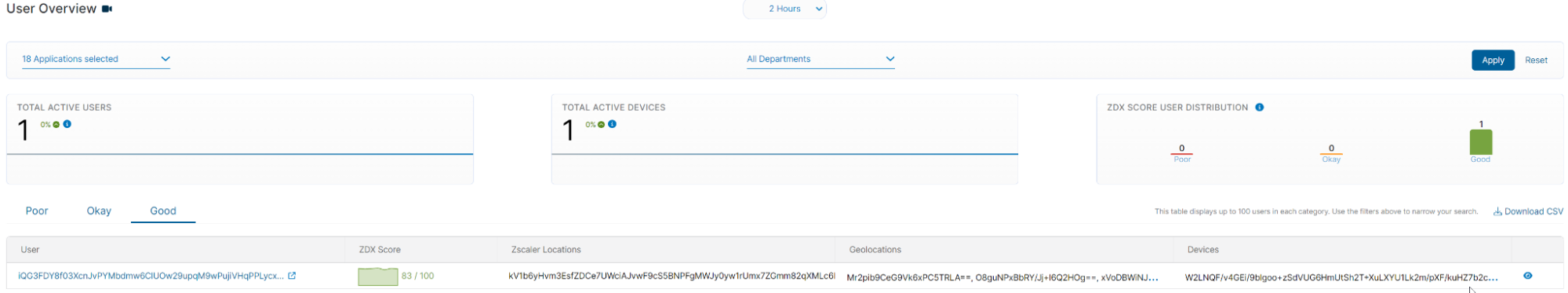
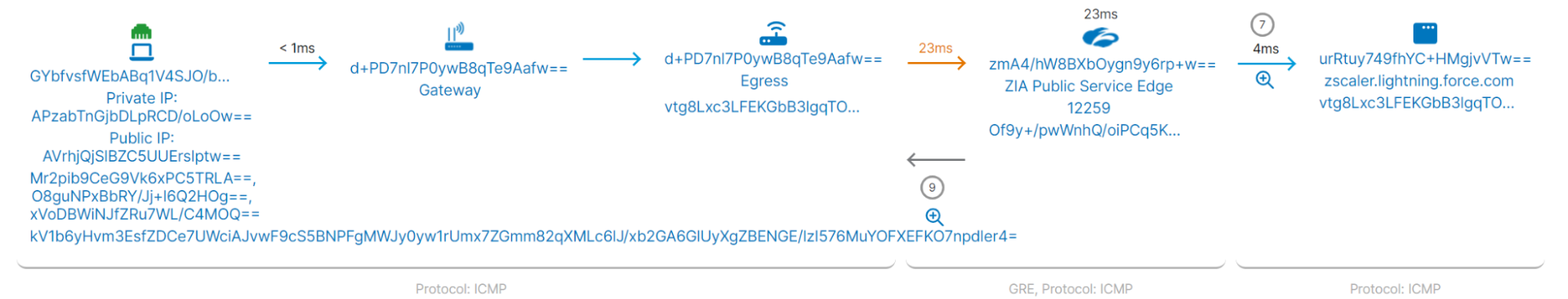
It is important to understand that application and network traffic data is acquired by synthetic monitoring, not actual user traffic. ZDX does not inspect actual user data in motion, so no information about visited websites or actual user activity is being monitored.
ZDX may integrate with third-party providers like Microsoft Teams, Zoom or Webex for meeting data. Content of those meetings is not collected, but metrics like meeting ID, duration of meeting, technical KPIs, and other meeting participants can be visible in the ZDX portal.
Personally identifiable information (PII)
ZDX collects the following PII information:
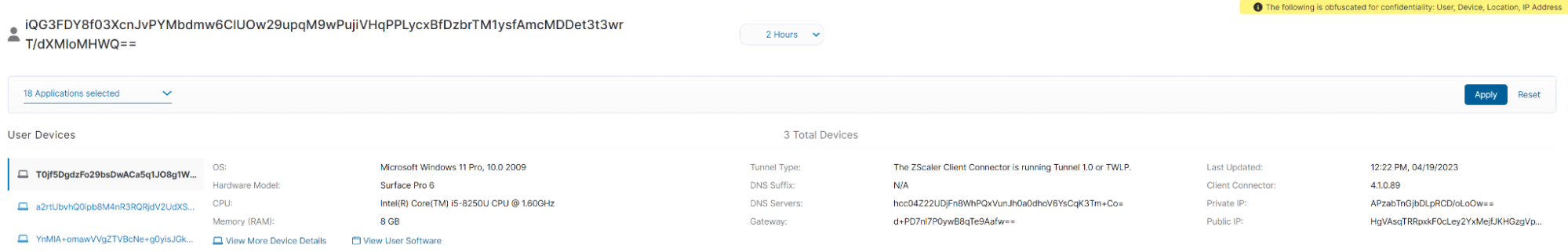
- Device IDs and device usage information. Zscaler Client Connector (ZCC) captures detailed device fingerprint and usage information.
- Device geolocation. ZCC can communicate with location services on a device and picks up the device’s geolocation coordinates. This is a configurable setting. If the coordinates are not available, geolocation is provided through IP address geo lookup for the internet-facing egress IP.
- Home network IP address. ZDX cloud path records the name and IP address of a user’s Wi-Fi network, including its SSID.
A ZDX administrator can configure ZDX and ZCC to protect user privacy and exclude PII entries. This includes:
- Login username
- Machine hostname
- MAC address of the network interface
- SSID and BSSID of the wireless LAN
Overview of controlling access
ZDX offers multiple layers of:
1. Collecting information
2. Giving access to the collected information
Define what information from whom to collect
Enabling and Disabling ZDX
ZDX is enabled on two different layers. First, ZDX is enabled in ZCC. This can be done either by selecting “ZDX Enabled by Default” to enable ZDX for all ZCC users, or it can be activated for specific User Groups.
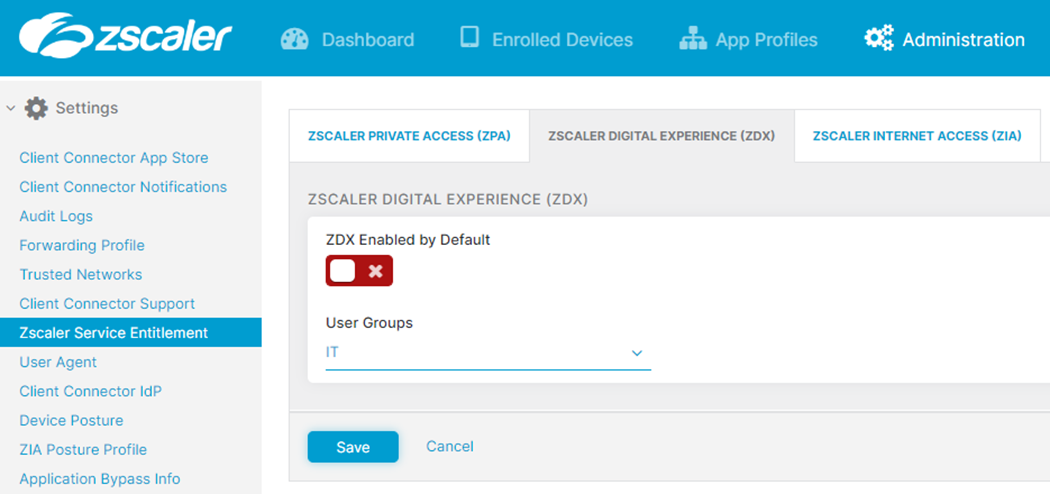
If you have enabled posture based services, there will be two more options, as you can see in the below screenshot. The Device Groups in this case will be taken from Posture Profiles. User Groups and Device Groups are connected with logical AND. A use case would be, for example, to differentiate company devices and private devices and enable ZDX only on company devices.
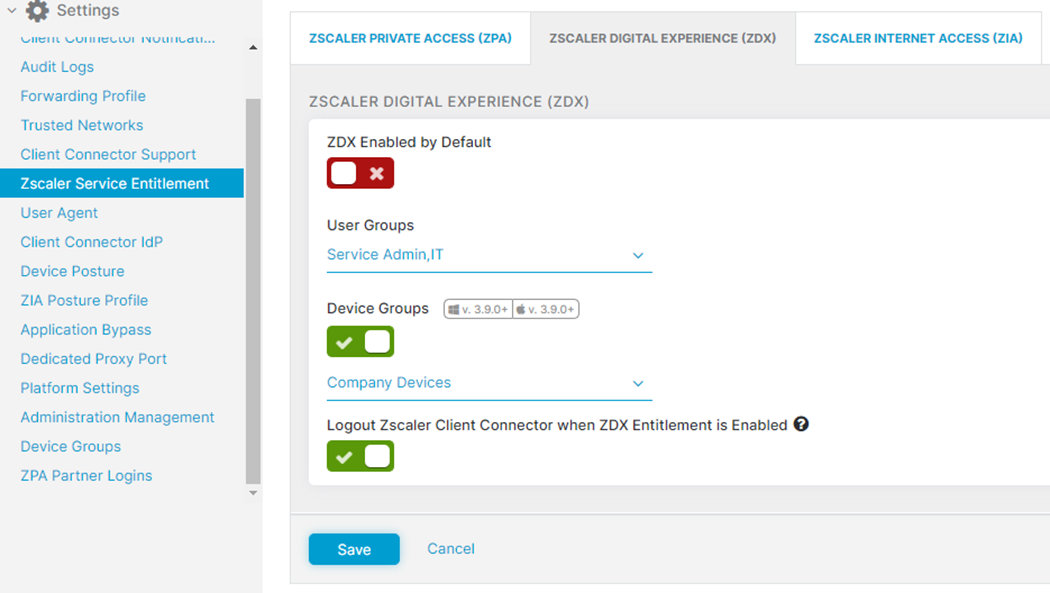
Users, User Groups, etc. for ZDX are taken from the ZIA repository. If ZIA is connected to AD, an option would be to use a specific AD group for ZDX. In the screenshot, you see that ZDX is activated only for the group “IT.”
Our recommendation is to have as many users active in ZDX as possible in order to be able to see global trends—geographically as well as for applications—so that in case of a decreased ZDX Score, actions can be initiated quickly to improve the digital experience.
Zscaler Client Connector user privacy options
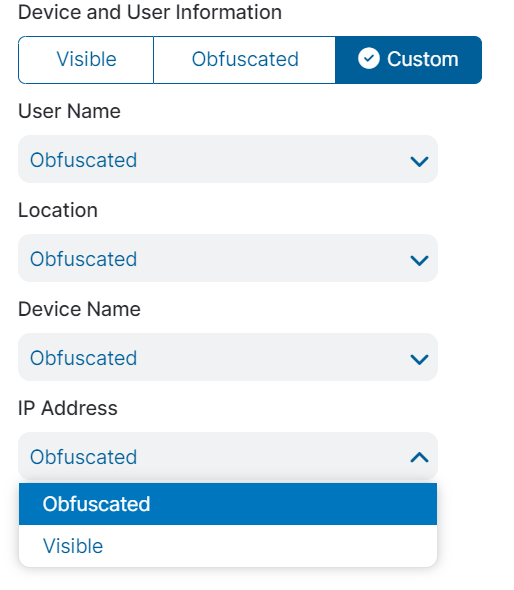
The configuration to protect PII information is controlled in Mobile Portal and at the administrator management level, where obfuscation can be enforced.
Please see the screenshot below for ZCC User Privacy Options. Those are not only relevant to ZDX, but used by other Zscaler offerings as well. Specific to ZDX are the two options “Enable Local Packet Capture in Zscaler Client Connector” and “Collect Location Info for ZDX.”
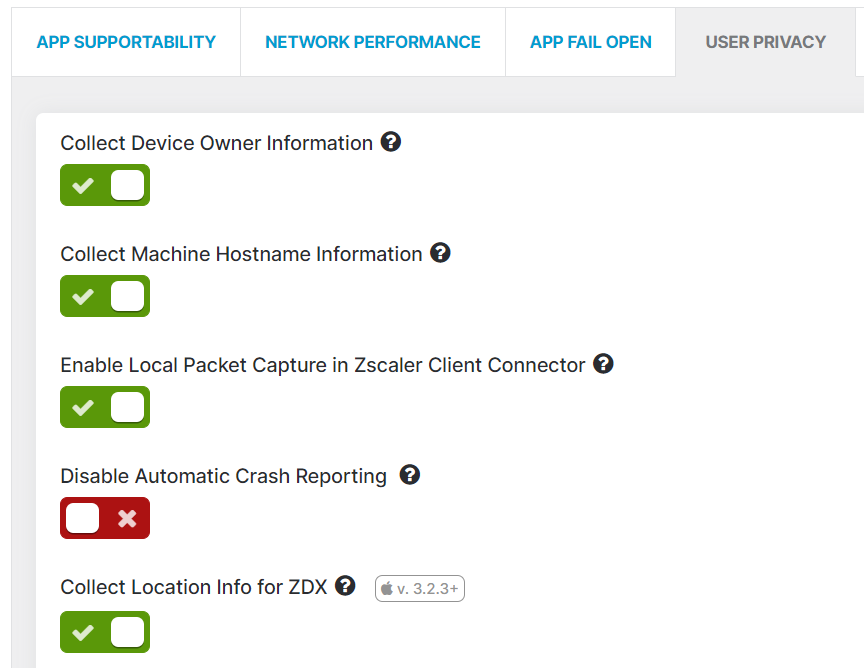
Sharing device location information
There are two mechanisms for collecting the user’s geolocation. The first method is to enable the collection from Windows device by enabling the collection in Mobile Portal.

If that option is disabled, the location is estimated by the egress IP address and the public/internet-facing IP address of that connection.
The second option is the default, that can’t be disabled, but can be obfuscated.
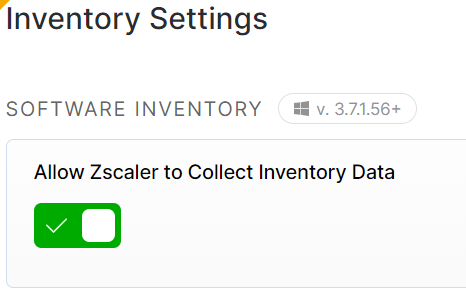
Device inventory setting
The collection of device software inventory can be enabled or disabled on a tenant level.
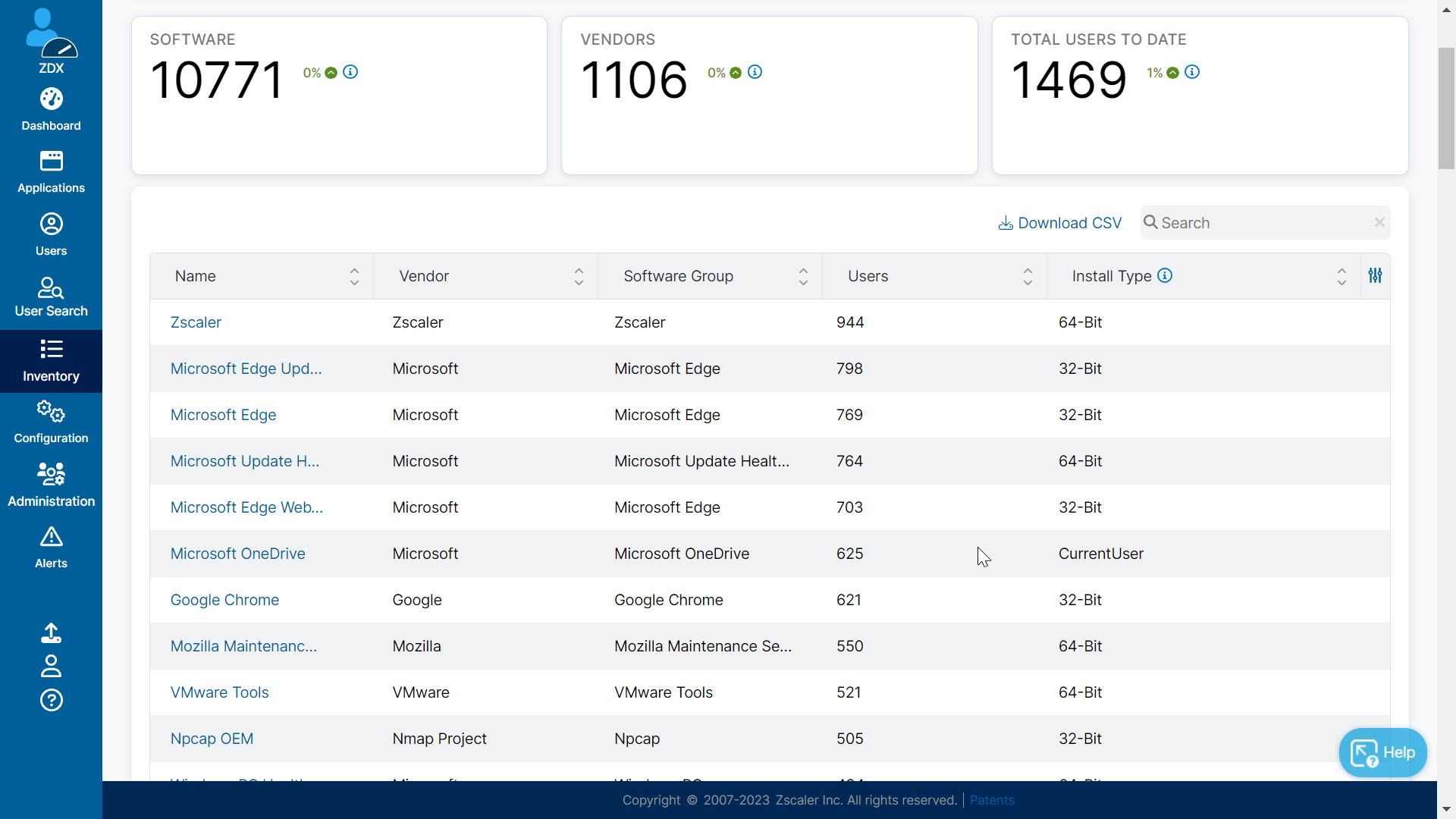
Sample of Software Inventory Overview
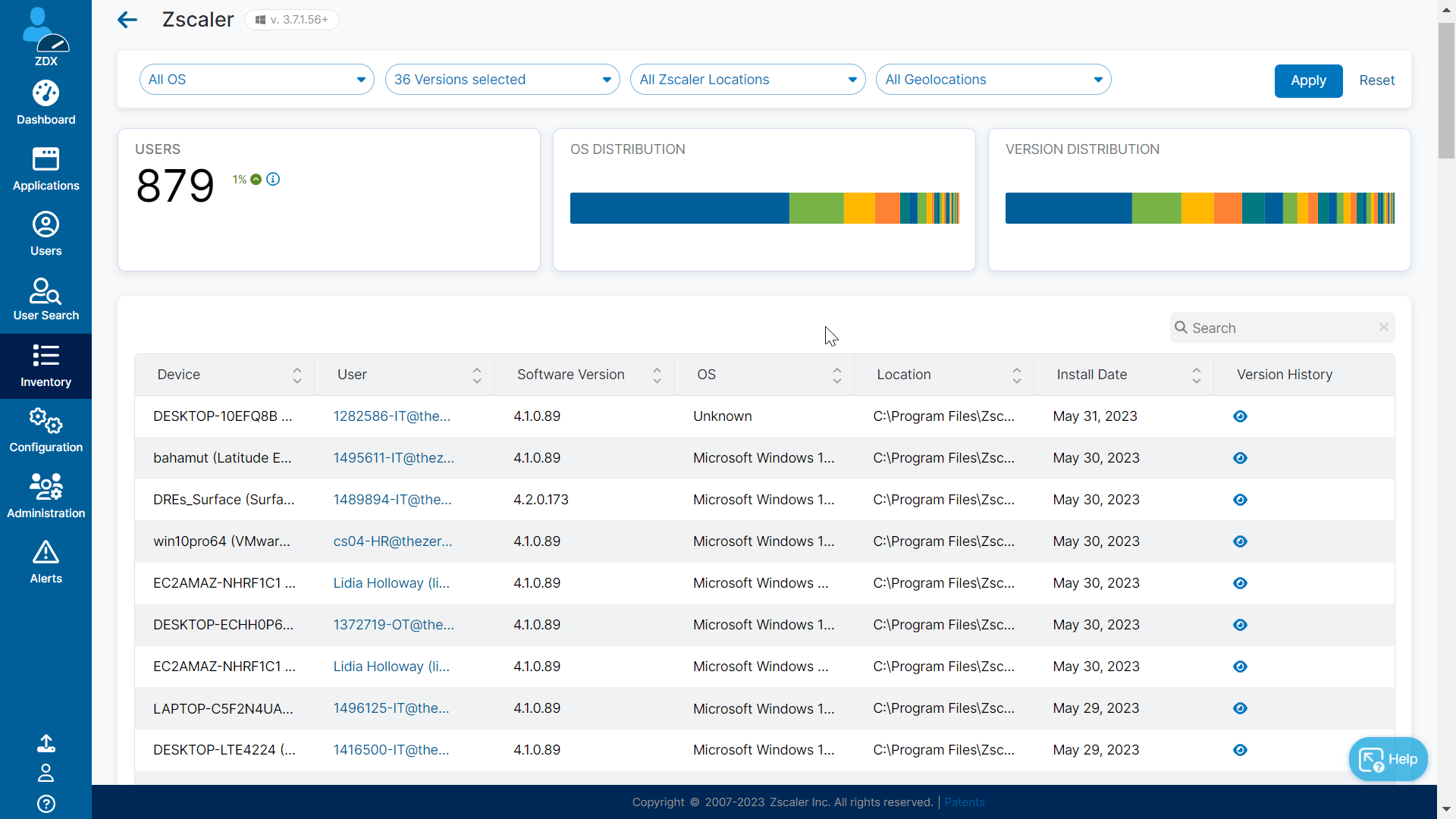
Sample overview for zscaler software
Enabling applications and probes

After the enablement of ZDX, applications and probes need to be configured. Those two can be assigned to all users or a subset of users.
Synthetic monitoring depends on applications and their assigned probes. Without any defined probes, no data is collected.
In the context of data protection, it is important to understand that for each probe the applicable users or groups, etc. can be defined. See the screenshot below for the available configuration options.
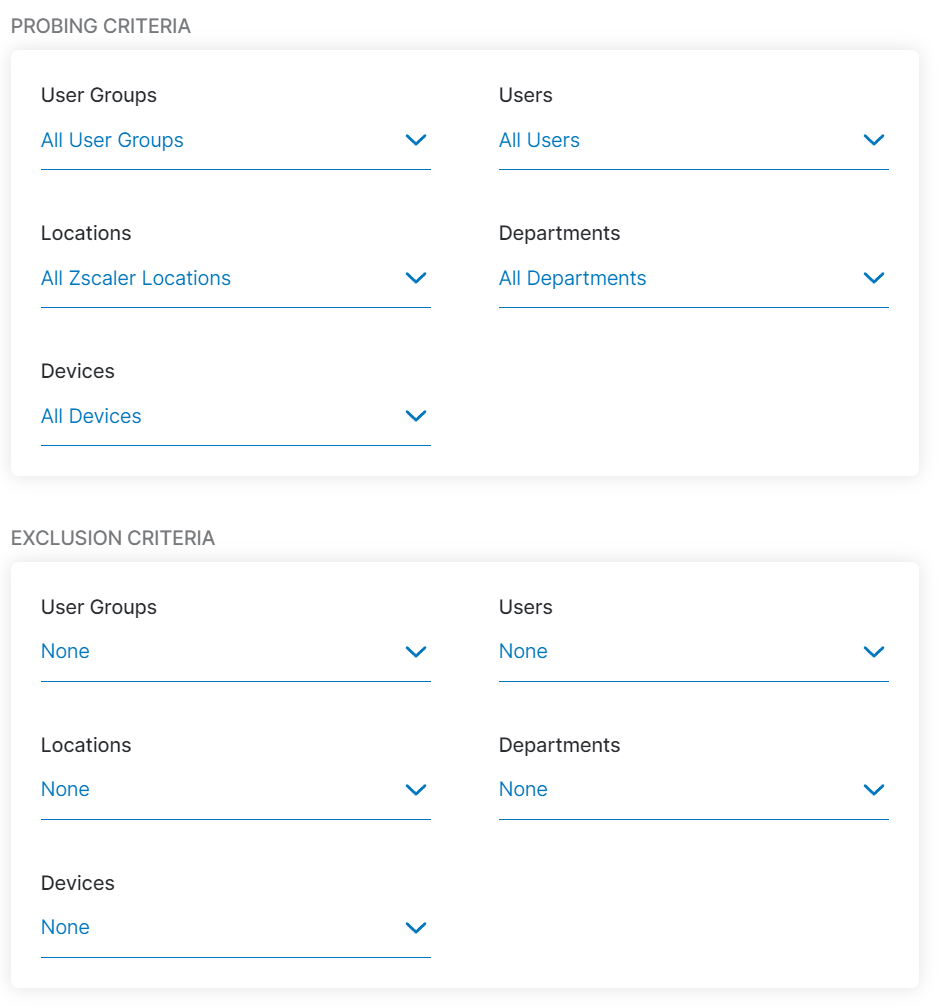
Controlled access to the collected information
Operational use and role-based access control (RBAC)
Only assigned administrators will be able to log in and see the data collected by ZDX. Additionally, ZDX has multiple means of protecting personal information of a single user.
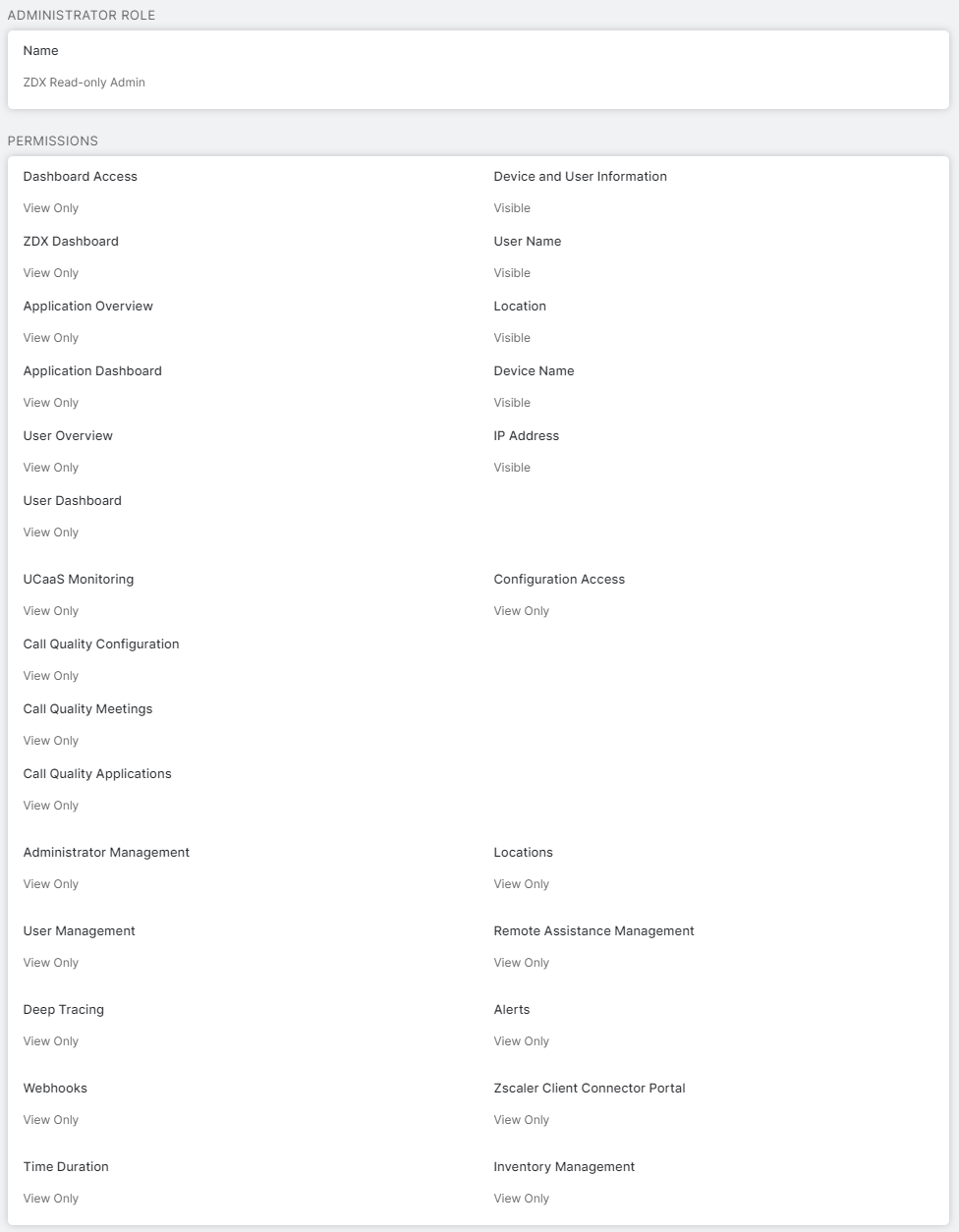
This is implemented by RBAC. Different roles with different permissions for certain aspects of ZDX and the collected data can be defined in ZDX to limit access as needed.
There are three predefined roles:
- ZDX Read-only Admin
- ZDX Service Desk Tier 1
- ZDX Super Admin
An example is presented in the following screenshot. Keep in mind that roles can be set up and added as needed for your organization.
Furthermore, each individual administrator can be assigned to a specific scope, organization-wide, or just a specific department or location.