Companies embrace Microsoft 365 (M365) to reduce IT complexity and drive end-user productivity and collaboration. Over 258 million people use the Microsoft 365 productivity and collaboration suite today. Featuring business-critical products such as Exchange, SharePoint, Word, Excel, PowerPoint, Outlook, and OneDrive, it’s not hard to see why it has become so popular.
While M365 brings a range of benefits to organizations and users alike, it can also introduce challenges to your overall security posture and to your security teams. According to IBM Security’s 2020 Cost of a Data Breach, the attacks directed at cloud services, particularly collaboration tools like Microsoft 365, have increased significantly. Remote work due to the pandemic has been a significant contributor to M365 security incidents, as attackers know that many people are working from home on unmanaged devices and connecting over unsecured networks or VPNs.
Security concerns are valid, as cybercriminals have shown that they’re more than capable of taking advantage of any security misconfigurations or shortcomings. One simple misconfiguration can expose an organization’s most sensitive data, leading to devastating financial and reputational consequences.
The challenge for the IT security team is not only protecting sensitive data against internal threats but also retaining security, compliance, and uniform policy enforcement. Unfortunately, with limited resources, tools, and budgets, IT leaders are asked to do more with less, such as ensuring a healthy M365 security posture, maintaining the secure and compliant use of M365, and remaining agile in the face of unforeseen events.
Microsoft 365 provides built-in policies, foundational and premium security controls, and systems. It analyzes 6.5 trillion signals every day to identify emerging threats. It includes native security at various levels (depending on your license). Overall, it does a good job securing data within its ecosystem, providing data protection within the operating system, applications, and documents, but it might not be enough for the enterprise.
According to Gartner estimates, “50% of Office 365 deployments will rely on third-party tools to fill security and compliance gaps as well as maintain consistent security policies.”
Six reasons why IT leaders should consider SSPM to protect their Microsoft 365 environments.
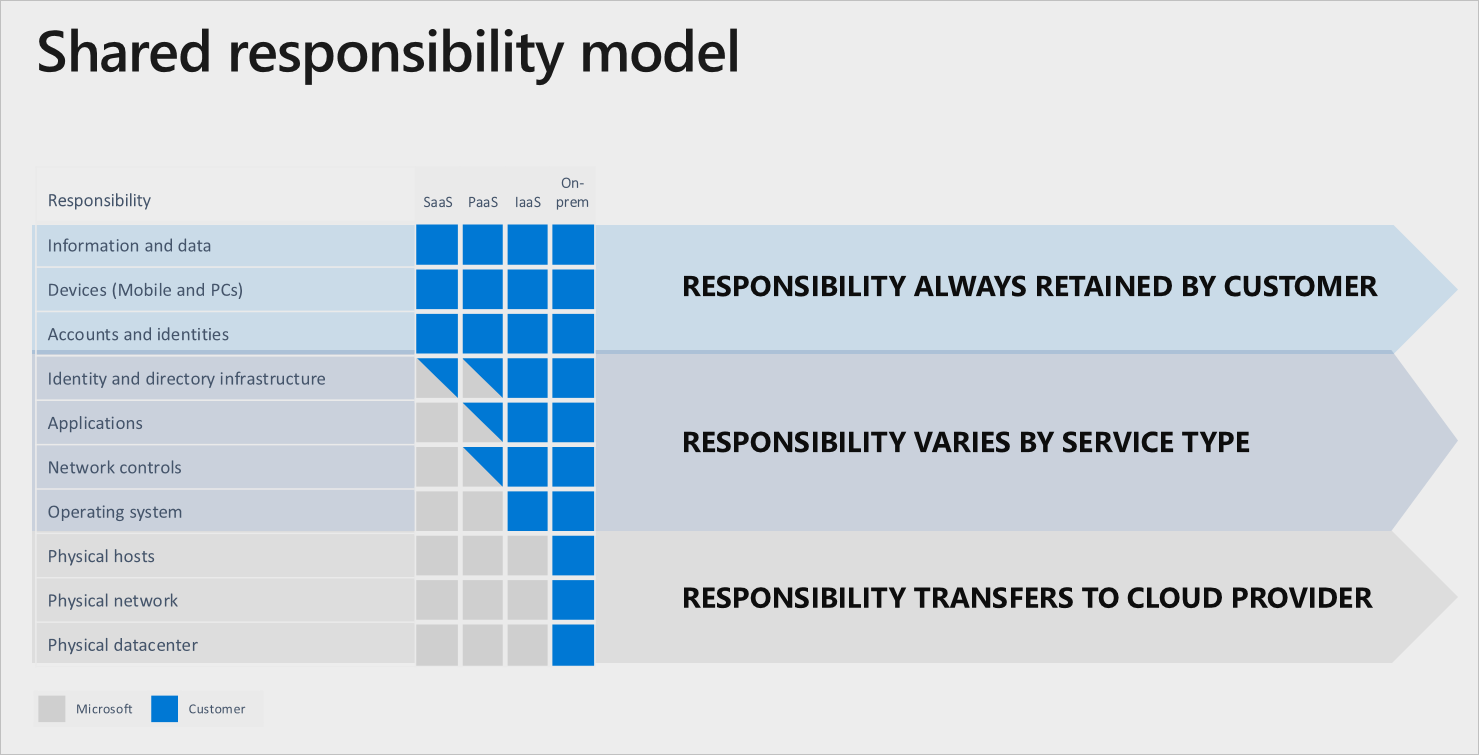
Reason 1: Shared responsibility – Enterprises are still responsible for M365 configuration, secure deployment, crucial data, and access to the data. Enterprise responsibilities also include assessing security and compliance and maintaining a secure posture by identifying and correcting potential threats before they result in a breach. Enterprises often overlook a critical M365 security consideration: how to automate the security posture of M365 to reduce the risk of data loss due to configuration errors.
Reason 2: Limited visibility – The increased use of the M365 platform compounds concerns about visibility, team collaboration, and increased surface attacks, and puts the enterprise at a high risk of ineffective control over M365.
Reason 3: Limited control over sensitive data – Data leaks and breaches comprise the most severe M365 security threats. Broad data and application access privileges must be allotted to certain users and administrators, but in a dynamic business environment, people tend to move around and change roles—unfortunately, their privileges don’t always change with them, leading to over-privileged access. Such users have the potential to change configurations or accidentally share sensitive data inappropriately. Excess privileges are risky and compromise security, especially with sensitive M365 data.
M365 and add-on apps make it easy to connect workers around the globe. But the M365 platform is primarily managed by the local administrator within the organization. Locally, manually managed applications are likely to drift out of security compliance over time and get exposed to internal and external threats.
Reason 4: Security and compliance enforcement – Regulated industries must comply with ever-changing rules, including SOC 2, ISO 27001, NIST CSF, NIST 800-53, as well as industry and government requirements, such as PCI, HIPAA, and GDRP. Most of M365’s compliance features are limited to the platform. Access to the compliance features varies from licenses and products/applications. It creates unnecessary complexity, business risk, and operational stress to enforce security best practices.
Reason 5: Rapid detection and response – The targeted attacks on M365 are rising in proportion to the growing adoption, which means that detection and response capabilities are essential. Enterprises need a proactive approach with automated risk detection through alerts and notification, policy enforcement, and guided remediation to mitigate the risk.
Reason 6: Operational challenges – Most enterprises do not have a dedicated SaaS security budget or expertise, and their tools are limited. M365 includes multiple applications, and each one can have hundreds of controls and settings that need to be continually adjusted and tweaked to adapt to the changing needs of the enterprise. M365 has no set default policies or settings that can be relied upon to provide the necessary accesses and functionality while maintaining the required security. Hence, M365 is often left unsecured by the security team due to limited budget, visibility, and expertise.
The solution
It's a challenge to maintain a secure M365 posture, protecting sensitive data, and enforcing a consistent set of policies and remediation actions. With the complex M365 configuration setup and limited control and visibility, M365 configuration errors will remain a central issue that enterprises must confront and ultimately overcome if they want to get the most from their Microsoft 365 capabilities.
Zscaler recommends an automated M365 security posture management approach with SSPM that identifies, prioritizes, and automatically remediates risk in a highly efficient and effective way. SSPM can audit sensitive configurations to allow automatic remediation of configuration errors and enforce critical security controls. Incident reporting and remediation workflow drive greater operational efficiency. Enforcing the same policies across all M365 services will also prevent policy enforcement gaps. SSPM, along with CSPM, will help you make the most of your M365 deployment and ensure that you continue to meet your security, compliance, and governance requirements.
Projected benefits of SaaS Security Posture Management (SSPM) for securing the M365 environment.
- Reduced likelihood of a data breach.
- Less time that IT and security teams must spend monitoring, assessing, and governing risks manually.
- Increased visibility and control over M365.
- Adherence to ever-changing industry compliance rules and regulations—audit-ready reports with ease.
- Ease of deployment, instant visibility and control, and no burden on the IT team.
Please connect with us directly to learn more about Zscaler CSPM/SSPM for M365 or schedule a demo.






