The foundation of a solid security model is visibility, deep insight into what is going on in a corporate network. Without visibility into applications, users, and network traffic, an IT team cannot make appropriate decisions about security controls.
Gaining visibility has become more complex, as users consume data over multiple types of devices and applications move to the cloud. But those changes have also made visibility more critical, as they’ve caused the attack surface of malware to grow exponentially, and they require security teams to significantly broaden their lens in order to maintain controls.
As a result, security teams are gathering as much data as possible from available sources: applications, systems, network sensors, and many other tools that provide insight into traffic and data flowing through the network. In addition, each security product — firewall, AV, sandbox, etc. —provides its own set of visibility with its own set of dashboards, formats, and color coding to help administrators triage events and alerts. Correlating all these different data sets presents a massive, time-consuming challenge that prevents security teams from moving as quickly as they should.
The need for context
While the key to security is visibility, the key to visibility is insight. All the many data points about traffic, apps, and users must coalesce into a narrative that tells a precise story of who, what, where, how, and when a security-related incident occurred in the network. To build this narrative model, context is paramount. The context in which an incident occurs is what gives IT teams the understanding they need to adapt the corporate security posture based on business requirements.
How do enterprises obtain this context?
A unified Internet security platform that can build context is what IT teams need to be able to read the storyline the corporate data flow is conveying.
Such a platform can provide information on the who, what, where, how, and when an event occurred, along with a clear view into what is happening on the network. Zscaler, with its cloud based security-as-a-service platform, enables security teams to build the context and provide the narrative by unifying all the network data into a single set of logs. The result is simplified access to data for security teams, enabling them to read the narrative and adapt the security posture to meet business demands.
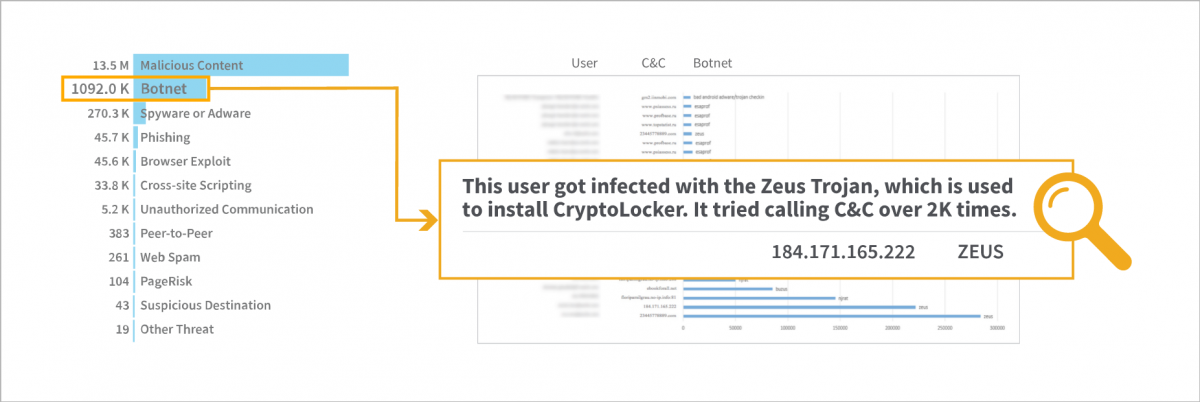
Zscaler provides multiple levels of visibility, from very broad views to deep details. In this report, the customer was able to identify and block botnet-infected machines that were calling C&C servers.






